DomainKeys Identified Mail (DKIM) is one of the 3 pillars of email authentication methods today. It is responsible for ensuring that the email’s sender is who they say they are by verifying the digitally encrypted signature added by the sending mail server. However, the DKIM authentication often fails resulting in the emails being rejected completely, or landing in the spam folder.
The DKIM check can fail due to multiple reasons. When it does, users have often reported seeing the following error in the authentication result (ARC) headers of the email:
DKIM Fail: Body hash did not verify
The error can often be slightly different, and can start with “DKIM Neutral“. However, the remaining error remains the same.
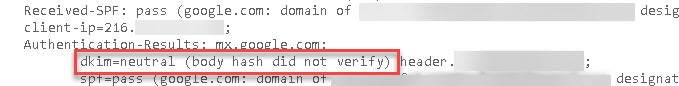
Table of Contents
Why the DKIM body hash failed verification
As mentioned in a detailed post on DKIM, the DKIM authentication works as a 2-part mechanism, where one part of it is in an email header, and the other part of it is in the DKIM DNS records. The DKIM record keeps the publically available encryption key, and the DKIM header contains the calculated body hash for the email.
When the “Body hash did not verify” error appears in an email header, it means that the calculated hash value of the message body did not match the value of the “bh” (body hash) tag stored in the email’s header. However, this can occur for any number of reasons.
Read about the different DKIM header tags and what they mean here.
Here are a few common reasons for the DKIM check to fail:
-
The email has been spoofed/hacked in transit
The whole purpose of DKIM is to ensure that the email contents are in their original state, as the authentic sender sent them, and that the contents have not been accessed/manipulated during transit.
If the contents of the email body have been altered after the DKIM signature has been added, the DKIM check will surely fail.
If this causes the DKIM check to fail, it also often means that the Transport Layer Security (TLS) connection has also failed, since its purpose is to build an encrypted tunnel for communication between servers. Furthermore, this would mean that, if configured, the MTA-STS also failed.
-
The mail body has been changed by MTAs
Mail Transfer Agents, or MTAs, that forward emails, often add a compliance footer text to a received email before automatically forwarding it to the recipient. At this time, the email has already been signed by the sending email server, and now, its content has been changed.
This causes the DKIM check to fail, since the body hash in the “bh” tag in the DKIM header does not correspond with the computed hash.
The error message for such DKIM failure results in “DKIM Neutral“, which means that the DKIM check didn’t pass, but there is nothing wrong with it either.
-
The signer miscalculated the DKIM signature
Another reason for the DKIM check to fail is the signing server miscalculated the encrypted signature to embed. If that happens, even when all DKIm configuration is correct, the DKIM check can fail with the error message “DKIM Fail: Body hash did not verify”.
-
The DKIM record does not exist
The DKIM record is not a necessity for email authentication but is recommended. It may be possible that the sending domain did not create a DKIM DNS record for authentication.
Another possibility is the incorrect configuration or incorrect syntax of the DKIM record. In this case, it would need to be fixed to mitigate the error.
-
Incorrect public key in DKIM DNS record
It is also possible that the DNS records are not correctly configured.
The DKIM DNS TXT record stores the public key using the “p” tag. It may be possible that the public key isn’t correct, and when the receiving mail server performs a DNS lookup for the DKIM records, it uses the incorrect key for verifying the signature, and it would never result in a corresponding value as the value of the “bh” header.
-
The DNS is inaccessible (DNS outage)
DNS outages or network issues result in broken communication between the mail servers and the Domain Name Servers. If so, the DNS lookup cannot be performed, and the DKIM records cannot be retired. This issue can also result in the error “Body hash did not verify”.
-
An issue with email providers
If you are using third-party email provider services, like Gmail, Outlook, Yahoo, etc., then it may be possible that their servers are experiencing issues, or are unable to handle the length of the DKIM key. This issue can usually be resolved by opening a support ticket with your email provider.
Moreover, if this is the case, you’ll notice that the error message “Body hash did not verify” only occurs while sending emails using a specific email provider, while the rest are working fine and authenticating DKIM checks.
-
DKIM not configured for third-party services
If you are using a third-party email service provider, make sure to include a DKIM record specified by them. Every ESP has its own set of instructions to follow and provides the users with a public key they must use for a valid DKIM authentication when using their mail servers.
-
Incorrect DKIM selector
DKIM authentication uses selectors in the email headers that specify which DKIM DNS record to use for the specific mail server. It may be possible that your mail server is using the incorrect DKIM selector, which either does not exist or does not contain the public key required for this particular ESP.
Implications of DKIM failure
If you have sound knowledge about how email verification works, you would know that either the SPF check or the DKIM check is required for a positive DMARC alignment. Therefore, if the DKIM check fails, it raises the chances of the DMARC check also failing, in which case, an email would not be delivered to the recipient, or would land in the spam folder.
If the DMARC alignment repeatedly fails, it would raise the ratio of unauthenticated emails for your domain, increasing the risk of landing on the blacklist.
That said, you would now understand that the “Body hash did not verify” has a domino effect on your domain and its email deliverability. Therefore, addressing this error should be a priority.
Fixing the “Body hash did not verify” error
Since there are several causes for the DKIM check to fail, you must follow specific instructions to first determine the cause of the error. Once the cause is determined, it will be easier to troubleshoot.
Check if correct DKIM records exist
The first thing you should do is verify whether the DKIM record for your domain exists or not. This can be quickly verified through our Email Security & Deliverability Checker here is how:
-
Open the Email Security & Deliverability Checker tool using a web browser.
-
Enter the name of your domain and click Analyze.
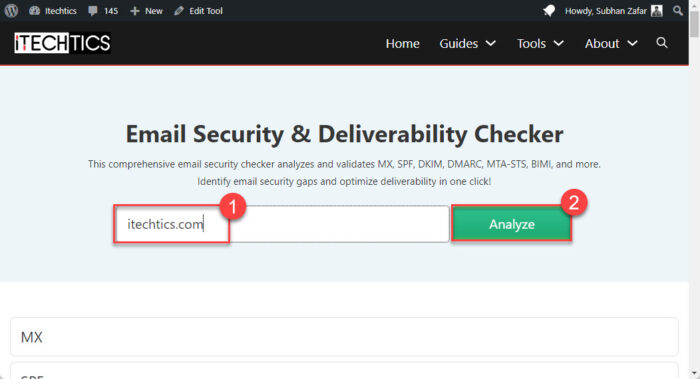
Analyze domain with Email Security and Deliverability Checker -
Check whether the DKIM records for the domain exist or not.
If they exist, the “DKIM” field will be highlighted in green with the record information showing. If it does not exist or the DNS is unreachable, the “DKIM” field will be highlighted in red and display “Record not available“.
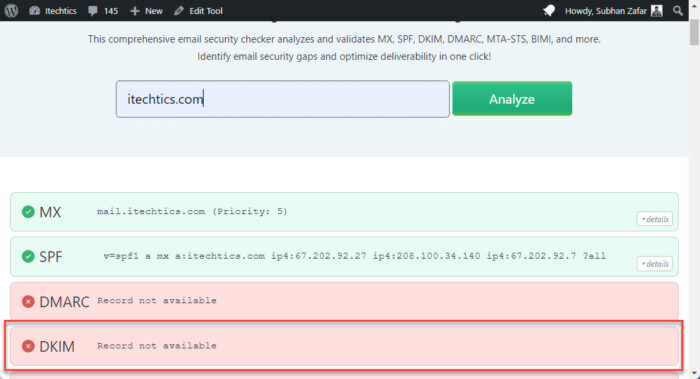
Check of DKIM records exist
After performing the steps above, if you determine that the DKIM records do not exist, then you must add them. Here is a complete guide on how DKIM records work and how to configure them:
What is DKIM and how does it work
Verify that MTA-STS is configured
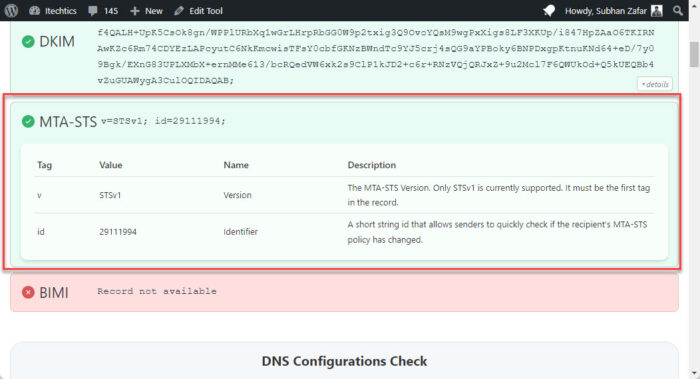
The purpose of Mail Transfer Agent – Strict Transport Security (MTA-STS) is to ensure that the mail servers use the TLS protocol to transfer emails. If it is configured, it means that the email that failed the DKIM check was using TLS, but still failed the check. This will rule out the possibility of Man-in-the-Middle attacks and your emails getting spoofed.
Our Email Security & Deliverability Checker also checks and grabs your MTA-STS records, if it is available. Similar to verifying the DKIM records, this tool will display whether the MTA-STS record is available for your domain, and display their tags and values if it is.
Verify email forwarders/gateway configurations
As mentioned earlier in this post, one of the causes for the DKIM check to fail is the addition or changes to the content of the email body by email gateways and forwarders. Since the DKIM signature has already been incorporated, these changes result in the DKIM “bh” header value not aligning with the computed hash of the message body, which in turn fails the DKIM check.
If you have access to those servers, check and prevent them from adding content to forwarded emails, or configure them to resign the email after they have been modified.
Check DKIM DNS records
You also need to verify that the DKIM DNS TXT records are configured correctly for your domain. This includes the record’s syntax, the tags being used, and the values set for them.
You can learn how to configure or edit the DKIM records here.
Moreover, make sure that you are using the Selector and the Public key specific by the email service provider if you are using one. Check that the DKIM key is valid and matches the one specified in your DNS records.
Use the “Quoted-Printable” Content-Transfer-Encoding
For sharing richer file types across the internet so all Mail Transfer Agents can process them, some encoding must be used. Emails use different types of encoding to transport the content between the servers.
As imposed by the SMTP protocol, there are limitations for certain servers to be able to process the different types of encoding. However, the “Quoted-Printable” encoding works well for DKIM.
As reported by a user here, changing the value for the “Content-Transfer-Encoding” header to “quoted-printable” fixed the “Body hash did not verify” issue they were experiencing with Outlook servers. According to the user, the Outlook servers were not able to handle the 8-bit encoding standards.
Consult with the Email Service Provider
If you have applied the solutions above and cannot figure out where the issue lies, I recommend that you now consult with the third-party email service providers.
As per my research, the issue often occurs on the ESP’s end, and since it is their servers, you have no control over them. In such a case, opening a support ticket with the ESP might be your best shot at fixing the DKIM check failure issue.
Conclusion
Both Google and Yahoo recently announced that all senders must have both SPF and DKIM enabled. With that, the spam rate for your domain should be below 0.3%, otherwise, your domain could be blacklisted.
That said, if the DKIM check fails, the chances of failing the DMARC check also increase, which means that your emails could be rejected, or sent to the spam folder. If this goes on for a while, your domain could be blacklisted. Therefore, do not take the “DKIM fail: Body hash did not verify” error lightly, and address the issue as soon as possible.

