Listening ports are ports that are currently in use by the computer. Ports are used to establish network connections between computers. Although the process of opening, listening, and closing network ports is seamless, identifying currently open or listening ports can help troubleshoot network-related problems.
Two major commands in Windows are used to check for open ports:
- Netstat (Command Prompt)
- Get-NetTCPConnection (PowerShell)
These commands can be a lifesaver for IT Pros and Sysadmins. This article describes how you can check for open and listening ports with Command Prompt and PowerShell.
Table of Contents
Types of listening ports
Before moving forward, it’s important to understand a few concepts about ports.
Open or listening ports are the ports that are being used by an application or program on your computer to establish a connection with another computer on the network.
There are two types of port connections in a Windows computer:
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
Different applications on a computer open different ports, some TCP and some UDP. UDP is less secure, but faster. TCP is slower but more secure.
Find listening ports with Netstat (CMD)
To check for open and listening ports, open Command Prompt as an administrator, and run the Netstat command as follows:
netstat -aOr
netstat -aon-a switch displays all active connections including TCP and UDP connections which the computer is listening to.
-o switch displays the process ID (PID) for each process.
-n switch displays IP addresses and port numbers in numerical form.
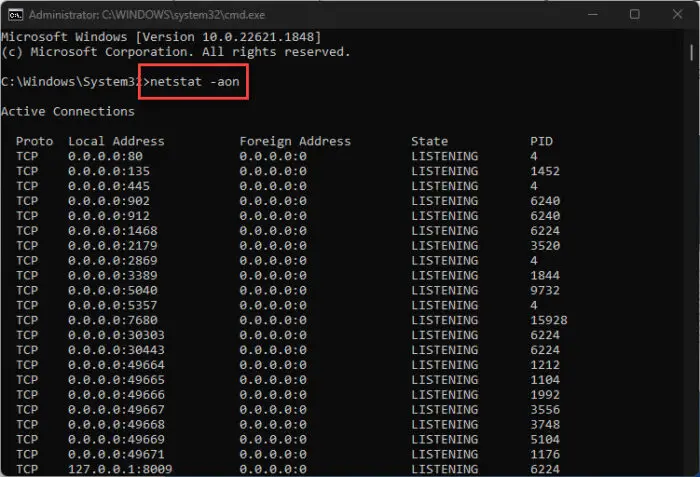
The output of this command shows the following items:
- Protocol (TCP or UDP)
- Local address (Your computer)
- Foreign address (Remote computer)
- State (Listening, Established, Time_Wait, Close_Wait)
- PID (Process ID of the process that has opened the port)
Under Local Address, the number after the colon (:) is the port number. If you only want to show the listening ports, you can run the following command:
netstat -aon | findstr /i listeningThis command lists the ports in the listening state.
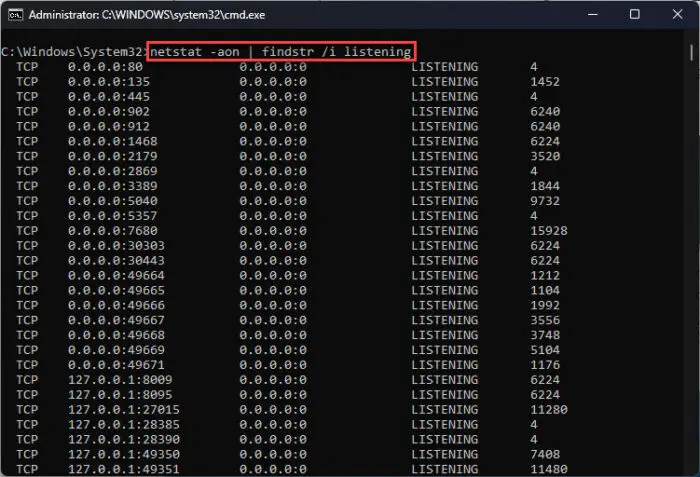
When you see “0.0.0.0:0” in the foreign address field, this means that this port is used in broadcasting. This can help in troubleshooting different network issues.
You can use the following switches with the Netstat command:
| Switch | Description |
|---|---|
| -a | Display all connections including TCP and UDP. |
| -n | Display addresses and port numbers in numerical form. |
| -o | Display process ID (PID) |
| -p | Show connections for a specific protocol. |
| -r | Show kernel routing table. |
| -s | Display stats by protocol. |
| -t | Display currently active connections. |
| -f | Resolves the IP addresses to fully qualified domain names (FQDN) |
| -e | Display network stats including errors, number of bytes, packets sent and received, etc. |
| interval | Time in seconds after which the command will run again automatically. |
Find listening ports with PowerShell
Get-NetTCPConnection cmdlet is the PowerShell equivalent of the Netstat command. It shows similar information to Netstat. You can find the following information using the Get-NetTCPConnection cmdlet:
- Local address
- Local port
- Remote Address
- Remote Port
- State
If you want to filter information, you can use the Where-Object filter which is similar to “findstr“.
Get-NetTCPConnection | Where-Object {$_.State -eq 'Listen'}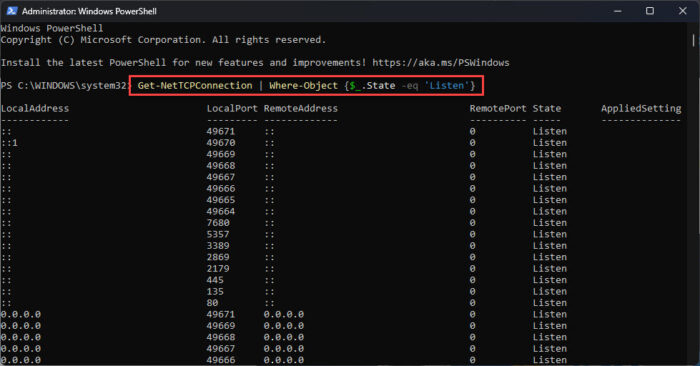
Alternatively, you can also filter the connection list by state using the -State parameter:
Get-NetTCPConnection -State ListenThis will show all the ports that are in the “listening” state.
Similarly, you can also apply the filter with a port number. Here is an example:
Get-NetTCPConnection -LocalPort 22You can run the following command for detailed information about each connection. Note that this generates a long list of information on every port.
Get-NetTCPConnection | Select-Object -Property *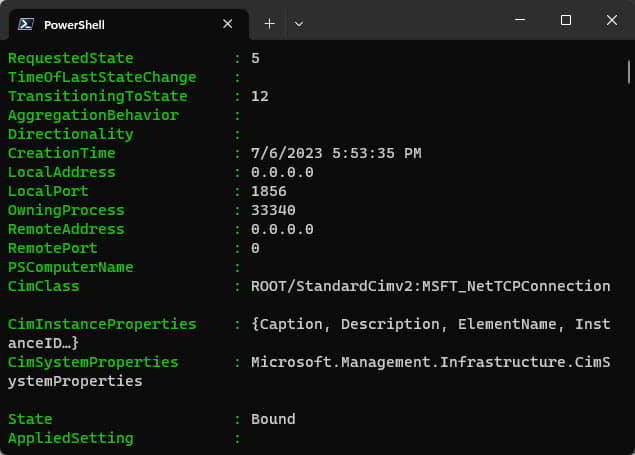
The main difference between Netstat and Get-NetTCPConnection is that Get-NetTCPConnection can be invoked remotely using the Invoke-Command cmdlet.
PowerShell also gives another command if you want to find open or listening ports on operating systems other than Windows, like Linux. GetNetStat is a cross-platform module that can be run on multiple computers where PowerShell is installed.
Once you have identified the open and listening ports, you can use this guide to close listening ports or block or allow websites, ports, and IP addresses with Windows Firewall. You can also find and close the app that has opened the relevant port.
This guide is for checking listening ports on a local computer only. You can follow this guide to check if the remote network port is open.